port forwarding
To use our port forwarding feature, simply connect to cryptostorm then visit http://10.31.33.7/fwd and follow the instructions there.
If you want to do port forwarding over IPv6, use http://[2001:db8::7]/fwd
On that page, choose a port between 30000 and 65535 then click the "Enable" button to activate the forwarding.
Next, you tell your Bittorrent client to use that port.
In qBittorrent and μTorrent it's under the Connection tab in the Options/Preferences:
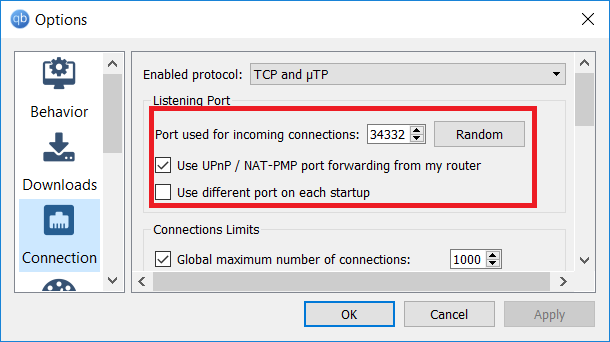
You should also go to the Advanced section in Options and change the Network interface to the VPN's.
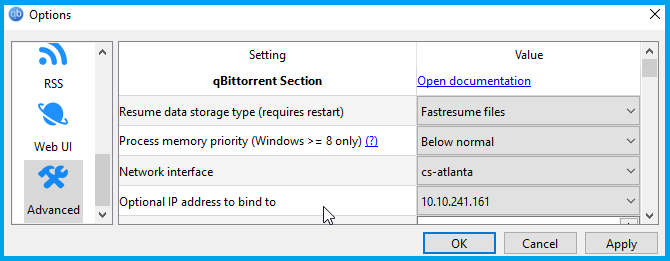
While testing on a Windows 10 system running WireGuard, it looked like:
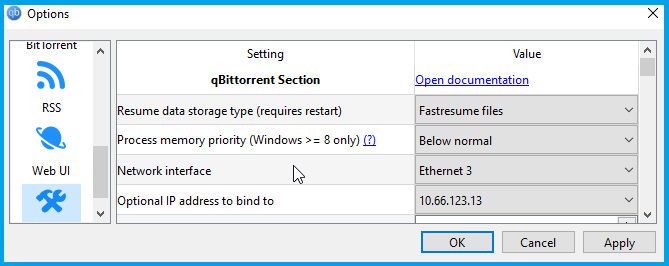
With OpenVPN, it looked like:
As you can see, the network interface name for WireGuard is obvious (cs-nodename).
For OpenVPN, the interface might be named something different on your system, especially if you have multiple TAP adapters from other VPN providers.
You should also make sure the IP address you're binding to is the VPN's.
It's always going to be something between 10.66.0.0 to 10.69.255.255 for OpenVPN, and 10.10.0.0 to 10.10.255.255 for WireGuard.
The IPv6 OpenVPN instances use 10.70.0.0 - 10.70.255.255 and fd00:10:60:*, and IPv6 WireGuard uses fd00:10:10:*
BitTorrent will still work correctly on cryptostorm even without port forwarding enabled.
The problem is that some peers in the swarm refuse to seed to peers who don't respond to direct connections.
With this setup, a temporary forwarding will be enabled between the VPN server's exit IP and your IP.
Your internal IP (10.x.x.x) is used for this forwarder, NOT your real IP.
Once enabled, you should see increased speeds for whatever you're downloading/uploading since more peers will now seed to you.
For OpenVPN users, this port forwarding is temporary. When you disconnect from the VPN, the forward will automatically be removed.
For WireGuard users, this port forwarding is semi-permanent. It'll stay active until you manually remove it, or your cryptostorm access token expires.
The port forwards are isolated to each individual VPN server (they're not network-wide). If you switch to a different server, the port forward would need to be recreated.
The limit is 100 port forwards per internal IP (per server). That means technically you can create 100 forwards from an OpenVPN session, then use another device to connect to WireGuard on the same server and create 100 more forwards. If your cryptostorm access token is of a duration that allows more simultanous sessions, each of those could do the same.
So if you had a lifetime token (which allows 6 simultaneous sessions), you could do 6 devices with OpenVPN + 100 forwards each, and 6 devices with WireGuard + 100 forwards each.
In that scenario, 1,200 forwards would be possible.
And no, port exaustion isn't a serious concern for us. The kernel-level max of 35,535 (65535 minus 30000) would be per external IP, and some of our servers have 100+ IPs. So on our server with the most IPs (114), in order to exaust every port forward a person would need 4,050,990 (35535*114) forwards, which would require ~3376 lifetime tokens. At $500 each, that's $1,688,000 they would have to spend in order to exaust the port forwarding options for a single server (or $844,000 if they wait for our yearly half-off sell we do every Black Friday to Cyber Monday).
We don't see someone wasting that kind of money on something like this.
And yes, we did take into account the "Port Fail" vulnerability disclosed by Perfect Privacy a few years ago.
Under a normal port forwarding setup, clients on the same VPN instance would be able to connect to each other, which could disclose a client's real IP.
We use a certain iptables rule that allows clients forwarding to still connect to other forwards, but their real IP would hidden.
If you want to do port forwarding over IPv6, use http://[2001:db8::7]/fwd
On that page, choose a port between 30000 and 65535 then click the "Enable" button to activate the forwarding.
Next, you tell your Bittorrent client to use that port.
In qBittorrent and μTorrent it's under the Connection tab in the Options/Preferences:

You should also go to the Advanced section in Options and change the Network interface to the VPN's.
While testing on a Windows 10 system running WireGuard, it looked like:

With OpenVPN, it looked like:

As you can see, the network interface name for WireGuard is obvious (cs-nodename).
For OpenVPN, the interface might be named something different on your system, especially if you have multiple TAP adapters from other VPN providers.
You should also make sure the IP address you're binding to is the VPN's.
It's always going to be something between 10.66.0.0 to 10.69.255.255 for OpenVPN, and 10.10.0.0 to 10.10.255.255 for WireGuard.
The IPv6 OpenVPN instances use 10.70.0.0 - 10.70.255.255 and fd00:10:60:*, and IPv6 WireGuard uses fd00:10:10:*
Before you begin to download anything, it would be a good idea to verify that your real IP isn't leaking using our torrent IP checker
BitTorrent will still work correctly on cryptostorm even without port forwarding enabled.
The problem is that some peers in the swarm refuse to seed to peers who don't respond to direct connections.
With this setup, a temporary forwarding will be enabled between the VPN server's exit IP and your IP.
Your internal IP (10.x.x.x) is used for this forwarder, NOT your real IP.
Once enabled, you should see increased speeds for whatever you're downloading/uploading since more peers will now seed to you.
For OpenVPN users, this port forwarding is temporary. When you disconnect from the VPN, the forward will automatically be removed.
For WireGuard users, this port forwarding is semi-permanent. It'll stay active until you manually remove it, or your cryptostorm access token expires.
The port forwards are isolated to each individual VPN server (they're not network-wide). If you switch to a different server, the port forward would need to be recreated.
The limit is 100 port forwards per internal IP (per server). That means technically you can create 100 forwards from an OpenVPN session, then use another device to connect to WireGuard on the same server and create 100 more forwards. If your cryptostorm access token is of a duration that allows more simultanous sessions, each of those could do the same.
So if you had a lifetime token (which allows 6 simultaneous sessions), you could do 6 devices with OpenVPN + 100 forwards each, and 6 devices with WireGuard + 100 forwards each.
In that scenario, 1,200 forwards would be possible.
And no, port exaustion isn't a serious concern for us. The kernel-level max of 35,535 (65535 minus 30000) would be per external IP, and some of our servers have 100+ IPs. So on our server with the most IPs (114), in order to exaust every port forward a person would need 4,050,990 (35535*114) forwards, which would require ~3376 lifetime tokens. At $500 each, that's $1,688,000 they would have to spend in order to exaust the port forwarding options for a single server (or $844,000 if they wait for our yearly half-off sell we do every Black Friday to Cyber Monday).
We don't see someone wasting that kind of money on something like this.
And yes, we did take into account the "Port Fail" vulnerability disclosed by Perfect Privacy a few years ago.
Under a normal port forwarding setup, clients on the same VPN instance would be able to connect to each other, which could disclose a client's real IP.
We use a certain iptables rule that allows clients forwarding to still connect to other forwards, but their real IP would hidden.
